Unauthorized Access
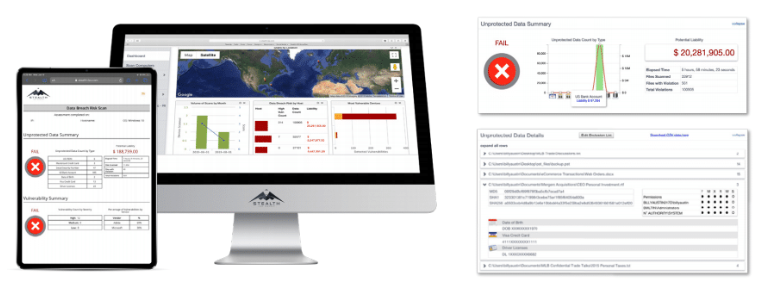
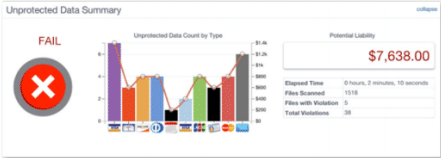
Most data is lost through human mistakes. Stealth Groupidentifies users with access to particular data sets.
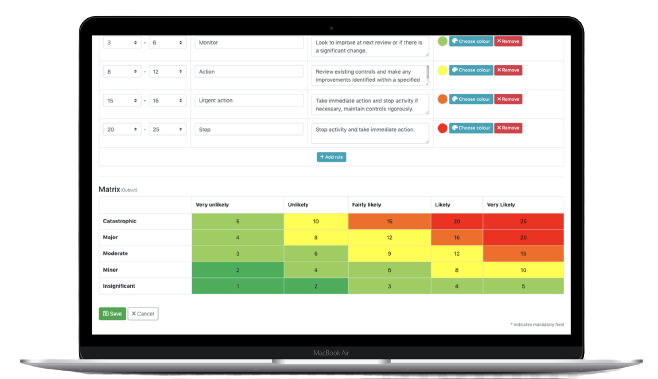
Vulnerabilities
Vulnerabilities allow thieves access to the data. Theseverity and number of vulnerabilities throughout theorganization is detected.