
| Quality |  |
5 |
| Value |  |
5 |
| Timeliness |  |
5 |
| Experience |  |
5 |
| Satisfaction |  |
5 |
| Overall Average |  |
5 |

Stealth-ISS Group® Inc.
BULLETPROOF CYBERSECURITY SOLUTIONS
MSSP and MDR Solution Brief
As cyberattackers increasingly target small and
medium- sized businesses (SMBs), Managed Security Service Providers (MSSPs) and other IT services providers are also coming under attack. By compromising the service provider, attackers have easy access to all connected clients. At the same
time, attacks on MSSP clients’ email, websites, and endpoints result in service disruption, high remediation costs for service providers, high downtime costs for clients, and loss of client trust.
Focus instead delivering proactive security services, providing remote support, developing new services, and handling ongoing business operations. By continuously ensuring that controls are effective, you can reduce business risk to you and your clients.
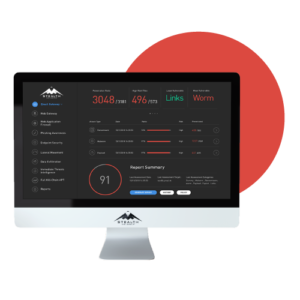
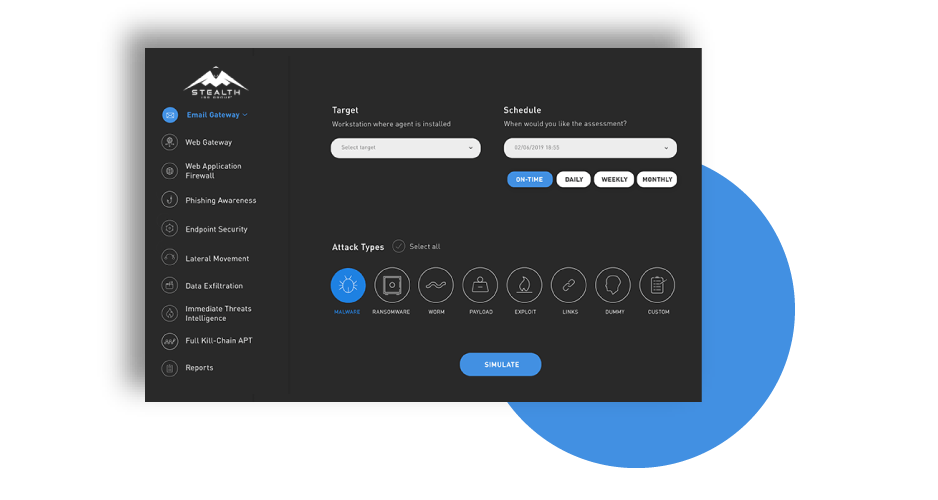
Breach and Attack Simulation (BAS) automated testing enables you to easily challenge, measure, and optimize security control effectiveness across the entire kill chain. Our BAS data delivers quantifiable metrics and actionable insights for improving readiness, preempting attackers, and reducing risk to clients and
your own business.
• Multitenant: Test security controls for multiple clients and your own infrastructure with detailed visibility into all controls and systems in a single pane of glass.
• Fast, cost-effective deployment: Run automated tests from a single agent, eliminating the need to deploy additional infrastructure.
• Safe simulation: Simulate attacks without jeopardizing production environments or burdening endpoints.
• Fully automated: Ensure testing repeatability and consistency while saving time for your technical teams.
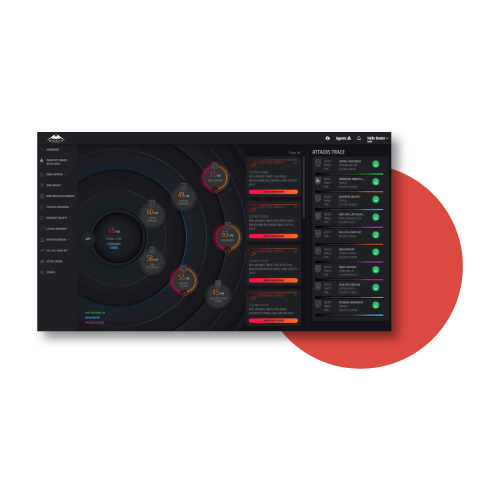
• Test across the entire kill chain or target specific vectors: Test against all threats, including the latest attacker tactics, techniques, and processes (TTPs).
• Flexible: Conduct testing at any time interval— continuously, hourly, daily, weekly, or as desired. Customize testing for each client’s environment, develop new revenue-generating services, and add value to current security offerings.
• Aligned with standards: Identify gaps and evaluate controls against the MITRE ATT&CKTM framework and remediate exposure with standards based guidance and actionable insights.
• SOC integration: Integrate with vulnerability scanners, SIEM, EDR, SOAR, and GRC solutions via API.

• Easy to use and manage: Highly visual and easy to use without requiring extensive security or testing expertise. Provides detailed data for all testing results, including events, alerts, and IOCs.
• Clear, easy-to-understand reports: Immediately create technical reports for SOC and technical teams. Executive- level reports can be provided to clients or packaged as added value to other offerings.
• Cyber support: We stand with your team to help them optimize their BAS testing capabilities.
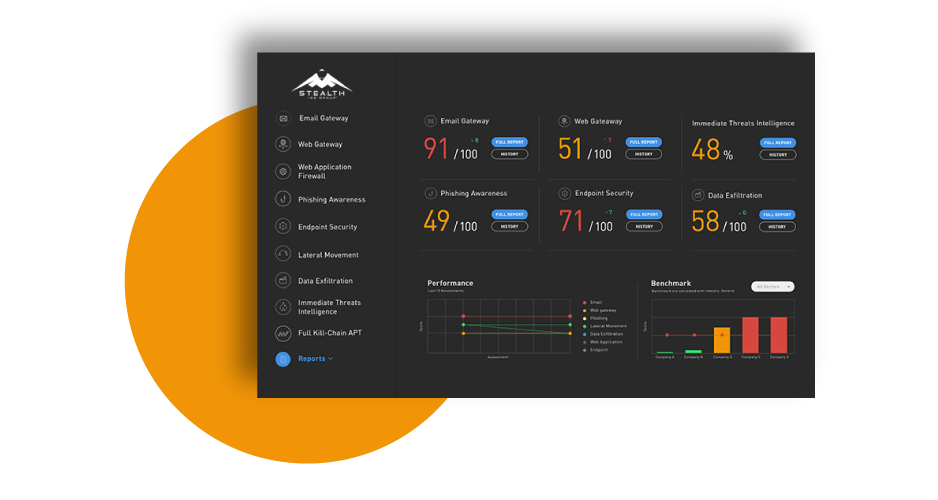
With continuous visibility into clients’ security controls, you have insight and data needed to optimize controls or recommend replacements.

Security posture assessment: Quickly and easily assess new clients’ security postures to support service recommendations. Continuously assess your own security posture to maximize protection, as well as to support competitive differentiation.
Security control validation: The ability to validate security controls across the kill chain and individual controls enables effective defense against the latest threats. BAS testing data documents effectiveness, provides guidance for improvement, and validates that remediation was effective.
Assuring SLAs: Continuous BAS testing enables you to assure that you’re meeting SLA terms with quantifiable detail to support service level pricing tiers.
Compliance audit readiness: Provide clients with compliance readiness services, enabling them to avoid audit findings and penalties.
Rationalize security spending: Use BAS testing to compare effectiveness of potential new purchases. Ensure that products under consideration deliver as promised and compare products based on testing results.
Uncover third-party and supply-chain gaps: SMB clients frequently lack the capabilities to successfully defend against threats targeting them through third-party and supply chain partners. BAS testing uncovers exploitable gaps, enabling you to prioritize remediation. Expand current offerings or create new
services to address supply chain vulnerabilities. Enhance red and blue teaming: Use BAS to complement red and blue team exercises.
Call 1-(866)-500-0751 or visit www.stealth-iss.com/

| Quality |  |
5 |
| Value |  |
5 |
| Timeliness |  |
5 |
| Experience |  |
5 |
| Satisfaction |  |
5 |
| Overall Average |  |
5 |
