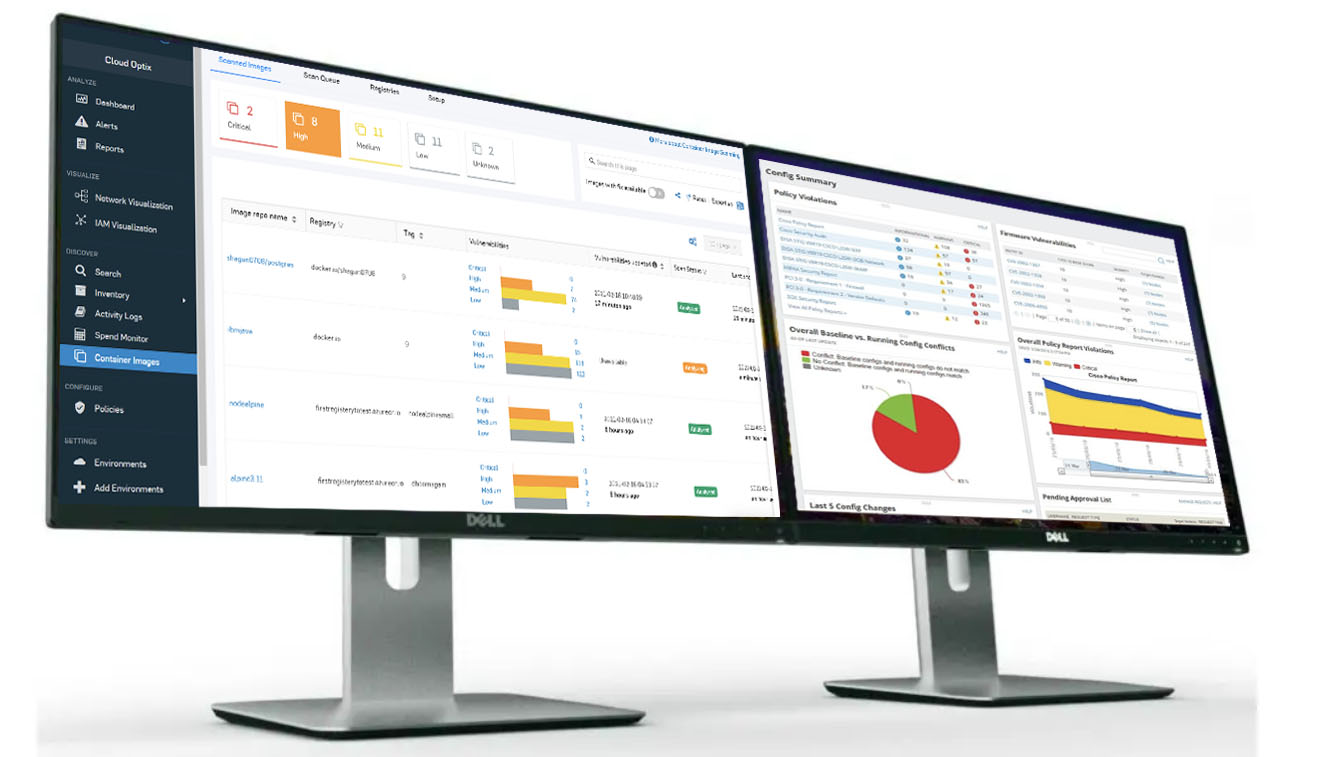
VISIBILITY TO IDENTIFY YOUR SECURITY THREATS AND REDUCE YOUR RISKS
Your vulnerability management needs daily attention. Stealth Group performs scan audits across your internal and external network devices, servers, web applications, databases, and other on-premise and cloud environment assets to identify your vulnerabilities and reduce your risk.
Unlike your traditional vulnerability management strategy, Stealth Group uses threat intelligence to analyze your vulnerable data and accurately determine the level of risk exposed to your company. This information, combined with specific, prioritized action items for your IT team, allows you to focus on efforts that are most likely to be exploited by attackers.